Published On Apr 25, 2024
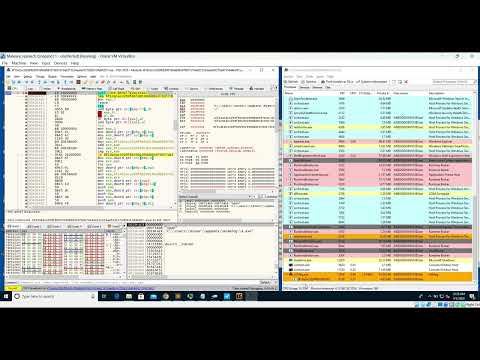
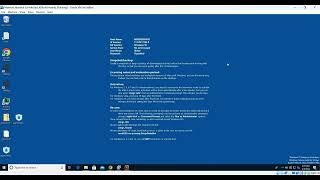
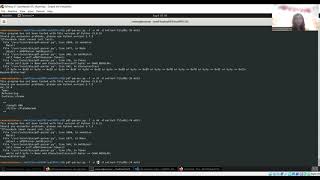
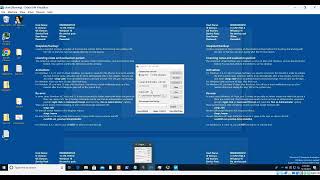
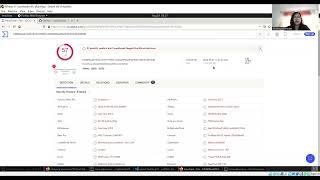
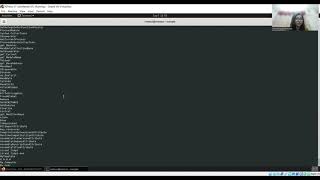
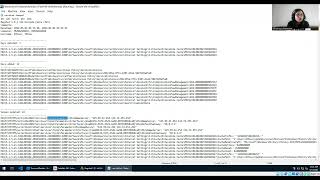
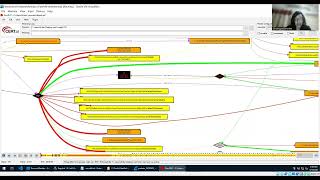
In this video, we are quickly analysing a malware which is a dropper and how we can get some basic details using a debugger. Again mostly, we have used very few tools to analyse and understand the intention of the sample. The sample used here is a recent malware, most probably belonging to RedlineStealer Malware Family.
Disclaimer: Please use a sandboxed environment for analysing malware
Samples:
6f10a5ac32b9f8b590199dd88c976057d19a6215224aafe45270dd3154d4b957
8E28A0090832A76CF71C417CB1BF7990B9AF86BE258B732117A47F624387083C
78B9D7E485026278B02A1961999AD99CDFA988FBF4403767DB5D10D1473E9870
Link to the Unpacked .net sample analysis - • Static Malware Analysis - .NET execut...
Linkedin: / shrutirupa-banerjiee
Twitter: / freak_crypt
Github: https://github.com/Shrutirupa
Instagram: shruti_jiee
#malware #learning #infosec #infosecurity #cyberattack #databreach #malwareanalysis #malwareattacks #malwaredetection #cyber #cybercrime
#staticanalysis #dynamicanalysis #debugging #cryptominer #redline #redlinestealer